According to the investigation conducted by experts at TrendMicro the number of HTTPS phishing sites is increasing and it will double by the end of 2014.

Google considers security a top priority for this reason the company is starting to use HTTPS as a ranking signal. The scope is to encourage the adoption of HTTPS, but the effort was understood by the cyber criminal ecosystem which is improving its techniques. Recently, experts at TrendMicro have discovered a phishing site using HTTPS and the case isn’t isolated, the number of phishing websites is increasing and researchers believe it can double for the end of the 2014.
The experts are also observing the adoption of HTTPS for mobile phishing. As explained by Paul Pajares, Fraud Analyst at TrendMicro, use HTTPS for phishingactivities doesn’t need a supplementary effort for cyber criminals, they can either compromise sites that already use HTTPS, or use legitimate websites that already use HTTPS.
“One of the reasons for this spike is that it is easy for cybercriminals to create websites that use HTTPS: they can either compromise sites that already use HTTPS, or use legitimate hosting sites or other services that already use HTTPS. There is no need for the cybercriminals to acquire their own SSL certificate, since they have just abused or compromised servers that do have valid certificates.” reports the blog post published by TrendMicro.
The post mention the case of a PayPal phishing page recently discovered, the threat actor used HTTPS and valid certificates and deployed the malicious page on a legitimate site that has been compromised. Looking for the “HTTPS” and lock icon in the address is not enough to trust a website, the only way to avoid to be victimized by this type of attacks is to carefully check the digital certificate presented by the website, it must be still valid and its common name is usually the same of the domain name.
The experts recommended not to use mobile devices for transactions outside authorizes apps from legitimate sources, but let me also add that many mobile applications lack in a correct management of SSL certificates advantaging the work of the attackers.
“We recommend that users need to check (via a search engine) that they actually are at the same URL of the company’s site. For example, users search PayPal in any trusted search engines if the URL received or accessed by the user is different from the site they’ve found through search engines, despite that it’s “https” and has “padlock” icon, then it’s probably a malicious site. If it is popular banks or financial institutions, the legitimate site will always appear as a top result. The next step is to check for certificate validity. Compromised HTTPS sites may have valid certificates, but users can still check the Certificate Common Name and organization before giving out login credentials. Note that certificate authorities have not issued certificates for malicious sites. The same thing could be said for desktops PCs.” recommended the post.
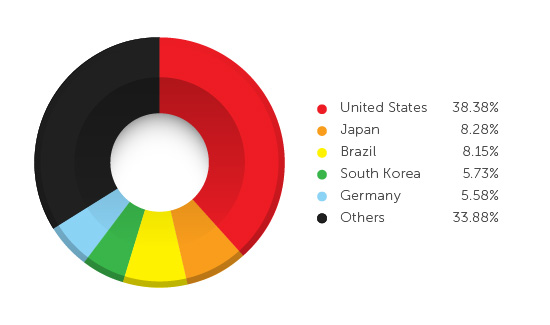
According to data provided by TrendMicro, US is the top affected country that visit HTTPS phishing sites (38,38), Brazil and Japan follow it at a distance in the ranking.
With the increasing use of SSL it is important to be aware that threat actors are anyway able to operate.
Pierluigi Paganini



Nenhum comentário:
Postar um comentário
Agradecemos sua participação.