
by Pierluigi Paganini on September 16th, 2014
Trustwave has detected a new series of attacks on servers worldwide based on the exploitation of old CGI-PHP vulnerability to spread BoSSaBoTv2 botnet.
It was 2012 when security experts discovered a security flaw (CVE-2012-1823) in some PHP builds that could be exploited by a threat actor to remotely execute commands on the affected server, if PHP was configured as a CGI script (PHP-CGI) at the time.
Security experts have recently discovered that the old CGI-PHP vulnerability is now exploited on a large scale to recruit machines for a botnet used with a primary purpose to mine Bitcoin. The researchers have detected different reconnaissance activities on a large scale, attackers were scanning for the above flaws in an automated fashion, and the operations were linked to various attacks over the years.
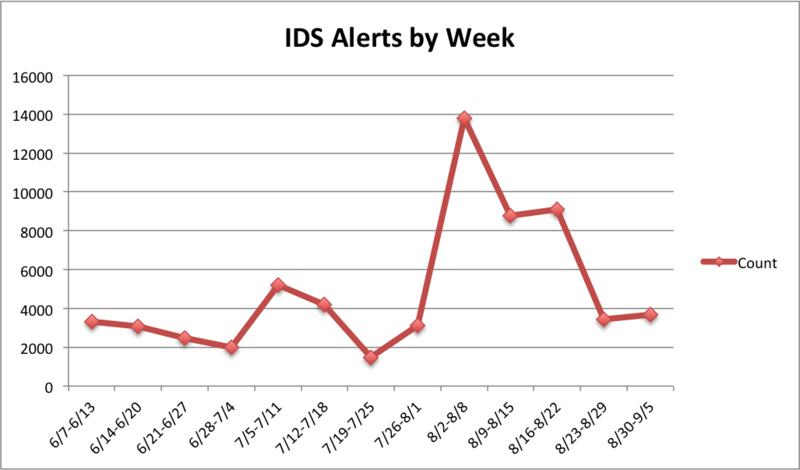
Trustwave, analyzing the traffic related to the spike in scanning activities detected in August, has noticed an uptick in attacks targeting the PHP-CGI vulnerability to deploy the BoSSaBoTv2 bot. In the same period, a researcher discovered an ad online offering the source code to BoSSaBoTv2 and just a few weeks later the malware was having risen in Internet again.
Once infected the machine, the BoSSaBoTv2 malware allows a remote attacker to control the servers using a shell or IRC. As explained in the blog post it could be used for Bitcoin mining as well as for DDoS attacks.
“Notice some of these features including bundling a Bitcoin Miner program. This is interesting as this shows another aspect how an attacker is looking to abuse their access to a compromised web server. They can siphon off local system resources such as CPU and RAM in attempts to create Bitcoins. Here are some of the commands for downloading and running the Bitcoin miner -” reports the post from Trustwave about the mining feature implemented in the BoSSaBoTv2 malware.
Below the statements used by the experts to introduce their discovery:
“Our web honeypots picked up some interesting attack traffic. The initial web application attack vector (PHP-CGI vulnerability) is not new, the malware payload is. We wanted to get this information out to the community quickly due to the following combined threat elements -
Active exploit attempts to upload/install the malware
The overall low detection rates among AV vendors
The malware is actively being sold in underground forums “
The worrying aspect of the attacks based on newer versions of BoSSaBoTv2 malware is the low detection rate for the binaries used in the recent attacks:
[Nome file 1] 5453043042be4ad21259bcb9b17e9bd3.exe
[Nome file 2] 097d995b242e387f4bdbfd2b9c9e5dfd9a33acc2_w00ted
The experts highlighted that the malicious code was written in C, a circumstance that is rare for the development of a botnet.
Once the attackers discover a vulnerable server, they try to install both 64-bit and 32-bit version of the BoSSaBoTv2 malware. According to the experts, bad actors mainly targeted businesses, that rent their servers or share them, because enterprise systems have the greatest computational capabilities and connect to faster communication cables.
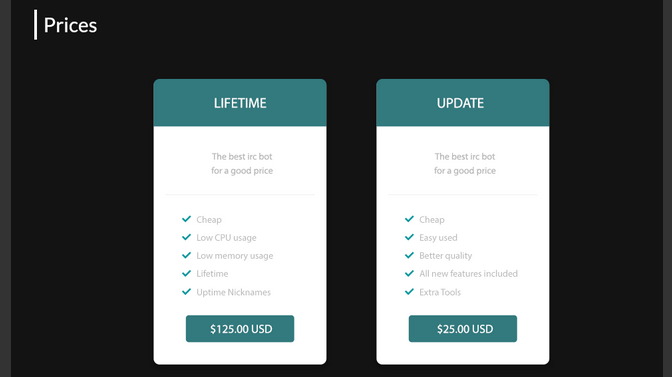
How much cost BoSSaBoTv2?
A fee for lifetime updates of BoSSBoTv2 malware costs $125, and the basic package is offered at $25 paying upgrades as extra.
Administrators could use as indicator of compromise the presence of strings containing POST variables that are Base64 encoded:
“Pay close attention to the HTTP Response Status Codes. Anything other than a 404 – Not Found could indicate trouble.” states the post from Trustwave.
another element to consider is that the following directories are being targeted during the automated scans we have described in this post:
Leia Também

Trustwave detectou uma nova série de ataques a servidores em todo o mundo com base na exploração da vulnerabilidade CGI-PHP BoSSaBoTv2botnet
It was 2012 when security experts discovered a security flaw (CVE-2012-1823) in some PHP builds that could be exploited by a threat actor to remotely execute commands on the affected server, if PHP was configured as a CGI script (PHP-CGI) at the time.
Security experts have recently discovered that the old CGI-PHP vulnerability is now exploited on a large scale to recruit machines for a botnet used with a primary purpose to mine Bitcoin. The researchers have detected different reconnaissance activities on a large scale, attackers were scanning for the above flaws in an automated fashion, and the operations were linked to various attacks over the years.

Trustwave, analyzing the traffic related to the spike in scanning activities detected in August, has noticed an uptick in attacks targeting the PHP-CGI vulnerability to deploy the BoSSaBoTv2 bot. In the same period, a researcher discovered an ad online offering the source code to BoSSaBoTv2 and just a few weeks later the malware was having risen in Internet again.
Once infected the machine, the BoSSaBoTv2 malware allows a remote attacker to control the servers using a shell or IRC. As explained in the blog post it could be used for Bitcoin mining as well as for DDoS attacks.
“Notice some of these features including bundling a Bitcoin Miner program. This is interesting as this shows another aspect how an attacker is looking to abuse their access to a compromised web server. They can siphon off local system resources such as CPU and RAM in attempts to create Bitcoins. Here are some of the commands for downloading and running the Bitcoin miner -” reports the post from Trustwave about the mining feature implemented in the BoSSaBoTv2 malware.
Below the statements used by the experts to introduce their discovery:
“Our web honeypots picked up some interesting attack traffic. The initial web application attack vector (PHP-CGI vulnerability) is not new, the malware payload is. We wanted to get this information out to the community quickly due to the following combined threat elements -
Active exploit attempts to upload/install the malware
The overall low detection rates among AV vendors
The malware is actively being sold in underground forums “
The worrying aspect of the attacks based on newer versions of BoSSaBoTv2 malware is the low detection rate for the binaries used in the recent attacks:
[Nome file 1] 5453043042be4ad21259bcb9b17e9bd3.exe
[Nome file 2] 097d995b242e387f4bdbfd2b9c9e5dfd9a33acc2_w00ted
The experts highlighted that the malicious code was written in C, a circumstance that is rare for the development of a botnet.
Once the attackers discover a vulnerable server, they try to install both 64-bit and 32-bit version of the BoSSaBoTv2 malware. According to the experts, bad actors mainly targeted businesses, that rent their servers or share them, because enterprise systems have the greatest computational capabilities and connect to faster communication cables.
How much cost BoSSaBoTv2?
A fee for lifetime updates of BoSSBoTv2 malware costs $125, and the basic package is offered at $25 paying upgrades as extra.

Administrators could use as indicator of compromise the presence of strings containing POST variables that are Base64 encoded:
“Pay close attention to the HTTP Response Status Codes. Anything other than a 404 – Not Found could indicate trouble.” states the post from Trustwave.
another element to consider is that the following directories are being targeted during the automated scans we have described in this post:
Leia Também

A Microsoft e o Google anunciaram seus planos para a desativação de certificados digitais SSL que utilizam o algoritmo SHA-1 Essa inic...


Nenhum comentário:
Postar um comentário
Agradecemos sua participação.